LockMagic AnyWhere File Encryption
Users encrypt documents and files on their local machine using LockMagic application and store the encrypted files on
local drive, flash drive, network share, Sharepoint
or cloud storage such as Dropbox or Google Drive. During the encryption
process, users specify the users and groups to grant access to the secure
content along with the access role such as Owner, Editor or Viewer. Other users
access the encrypted content using a LockMagic client
and depending on the access role granted the recipient user may be able to own
or view-only the content.
For
example, users can protect WORD files and share them using email, cloud storage
or flash drive. Authorized users can access the encrypted files using their
identity without have to share keys or passwords. Users with viewer-role will
only be able to view the WORD files on the screen and are prevented from
copying the secure content via the clipboard, print-screen, snipping or
printing.
LockMagic AnyOne Email Encryption
Lockmagic integrates with
Microsoft Outlook Email client to provide seamless end-to-end encryption.
One-Click ‘Send Secure’ button to compose encrypted email messages directly
from Outlook application. Email messages are automatically encrypted along with
attachments using recipient identities for authorization. There are no end-user
actions required to enter password or lookup recipient keys.
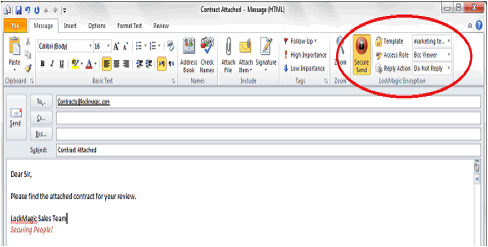
When receiving an encrypted message the LockMagic extension will automatically open the message
when viewed in the reading pane or form. The message and its attachments always
remain encrypted in the outlook local files and remote email server.
Reply and Forward actions of encrypted messages
retain the original message encryption property and users are not overwhelmed
with re-encryption processes.
LockMagic Exchange Outlook Web Access Protector
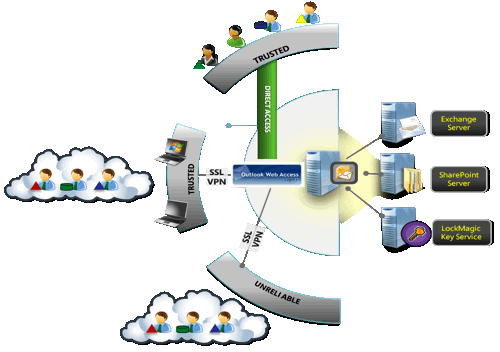
LockMagic integrates as an extension application to Exchange Outlook Web Access (OWA) in a simple and seamless manner. LockMagic for OWA is a Net.ASPX application that enables users to send, reply and view secure email messages over any web browser. Unlike traditional solutions, encryption and decryption are performed inside the client web browser.
Outlook Web Access is
deployed as part a Client Access Server that runs independent from the Exchange
Store Server. The LockMagic application consists of a
set of ASP.NET pages and a managed HTTP transport handler. It is solely
deployed on the Client Access Server with simple configuration updates.
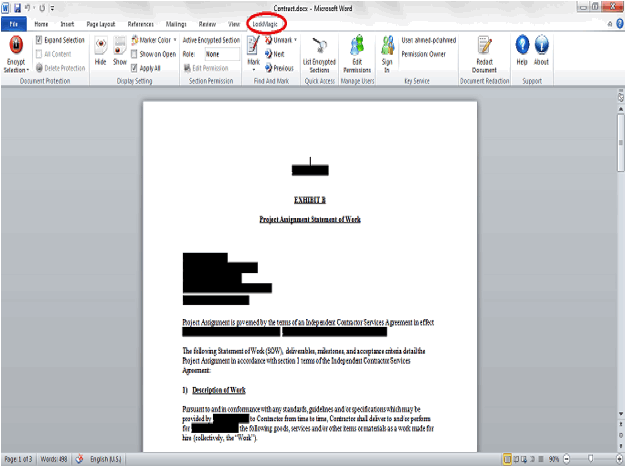
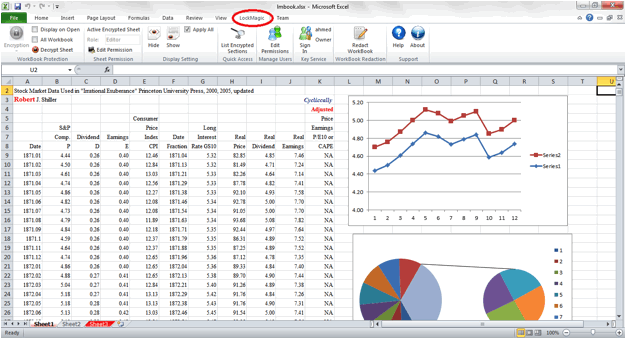
LockMagic Partial Content Encryption
There are many situations when users want to maintain a single copy of
a document or spreadsheet to share with multiple people but control which parts
of the document other users can view. LockMagic has
plug-ins for Microsoft Word and Excel that enables users to encrypt specific
parts of the document and spreadsheet eliminating the task of users maintaining
multiple copies for different users. Based on the user role, only the authorized
parts of the document can be viewed or edited.
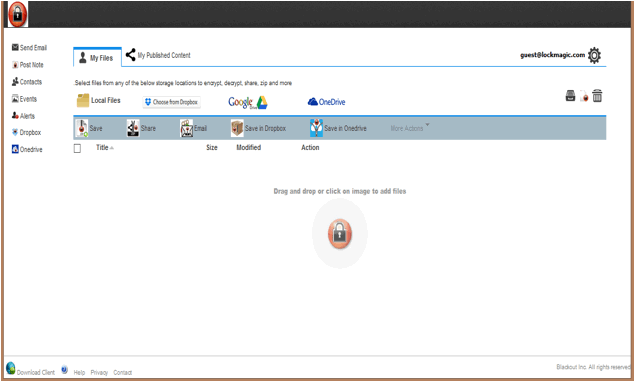
LockMagic Client-less Deployment
In many situations users don’t want to install any software on their
local devices to encrypt and decrypt content.
Lockmagic offers a browsed-based HTML5
solution that enables users to encrypt and decrypt content directly inside
their web browser. All cryptographic operations are performed inside the client
browser without any clear data ever transmitted over the network.
This feature simplifies sharing of secure content with partners and
external users and eliminates the need to install client software. Furthermore,
users have the ability to access secure content from mobile phones and tablets
without installing any application.
Onedrive and Dropbox
users can directly access their data through LockMagic
web site and transparently encrypt and decrypt content on the fly all happening
within the local browser. No clear data will be transmitted in the network or
stored in the cloud. Users can access to all functions such as copy, rename,
create folder, share, delete and manage permissions directly from the same
page.
LockMagic Content Revocation
LockMagic offers users complete control over
content with support for per-document expiry and revocation model. Authors
always retain control over their content even after the content has been shared
with others. Sharing can be assigned an expiry deadline after which the content
becomes inaccessible.
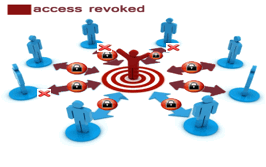
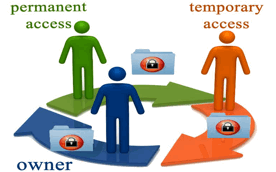
LockMagic per-document revocation model enables
content owners to revoke access to shared content at any time to retain control
over it. For example, an external partner may have been granted viewer-only
access to some sensitive information that the partner is no longer authorized
to access. The partner access can be revoke even though the partner has
possession of the encrypted content. After revocation the partner will not be
able to access the encrypted content and because the partner is only granted
viewing rights, the secure content couldn’t have been copied, printed, snipped
or print-screened.
LockMagic Application Integration (SDK)
LockMagic is designed and implemented with
extensible in mind offering a software-development kit (SDK) in several
languages and platforms including C, Objective C, Javascript,
Java and C#. The API is extremely easy to use given the nature of the
state-less identity-based architecture. Custom applications can easily
integrate LockMagic functionality with little effort.
LockMagic own Microsoft Office plugins and web portal
are implemented using the SDK APIs and libraries. The platform is available on
any device ranging from desktop to mobile devices.
LockMagic Strong Authentication
LockMagic integrates with two-factor
authentication systems to require strong user authentication when accessing
encrypted content. This ensures that high-value information remains protected
beyond a simple username and password. Furthermore, LockMagic
supports smart-cards and HMAC-based tokens for mobile encryption to ensure
endpoint systems remain free from any user keys. The loss or theft of a laptop
when LockMagic encrypted content remains secure
because the laptop hard disk doesn’t contain any keys or secrets that a hacker
can then use to gain access to the encrypted content.
A single LockMagic hardware token can be
configured for dual purpose to provide a One-Time Password for user
authentication to the LockMagic Key Server and the
same token along with a user-defined PIN and HMAC-SHA1 to derive a per-user
master encryption key.
Enterprises can bind tokens to external partners and contractors
private identities and grant them access to the enterprise LockMagic
key server without provision identities in the enterprise identity system.
External users can author, share and access encrypted content with enterprise
users in a normal fashion. For example, a contractor may use his Gmail identity
along with LockMagic hardware token to gain access to
LockMagic encrypted content. This is achieved without
any password or certificate management among users.
